Overview
This series discusses on the security on higher level so it doesn’t get too technical and is aimed for IT service owners and decision-makers. Focus is on prevention rather than the aftermath after something’s gone wrong.
Topics
Why – Why someone tries to access the environment?
Who – Who should be able to access the environment? Can we authenticate the users or identify them in another way?
Where – Where are the users connecting from? From the office network? Some specific country/countries/region? Can we either whitelist or blacklist the locations?
When – Is the environment accessed around the clock? Can we recognize peak usage times?
How – What kind of device they’re using, what possibilities we have locating and authenticating the user?
I think there are two levels of attacks to IT environments; vandalism – “let’s sweep the area and see if we can break anything” and the more dangerous one – targeted. I would say there are different measures one should take to be protected from these.
This post drills down to very basics, more will follow.
Vandalism
Someone just sweeps the network for known vulnerabilities and uses these to cause service distruption. The attacker doesn’t really care whose environment they’re breaking, but might use the stolen data to sell it forward or blackmail the company.
There’s plenty of tools that are really easy to use for this kind of activity and the attacker just might get their kicks just from causing an outage to a company access portal or web service. I would consider Denial-of-Service (DoS) attacks as one form of vandalism (ofc… targeted DoS attacks are certainly a thing also).

Targeted
Attack might occur on multiple vectors including social engineering, targeted phishing, etc… Protecting from these kind of attacks is much trickier and can’t be only prevented with technical measures.
One charasteristic for these attacks is likely doing subtle tests for the targeted environment on many levels just to check if there are one or many ways to gain access. My take is that a targeted attack is likely to be done “in the shadows” so that no one notices anything before it’s too late.
Protection
It takes way less effort (and money) to act in advance, because repairing damage after an attack takes a lot of work and money and there are things that one might not be able to fix like company’s reputation.
There are plenty of measures to protect the IT environment from attacks that fall in to one or both of the categories above.
Posture
One obvious thing is to avoid being an “easy target” and I think this applies for the both cases. Great ways to easily check your current security posture, is to use great free online tools like:
- Qualys SSL Labs SSL Server test (https://www.ssllabs.com/ssltest/)
- Security Headers (https://securityheaders.com)
Make sure you get the A+ or A grade for your site:
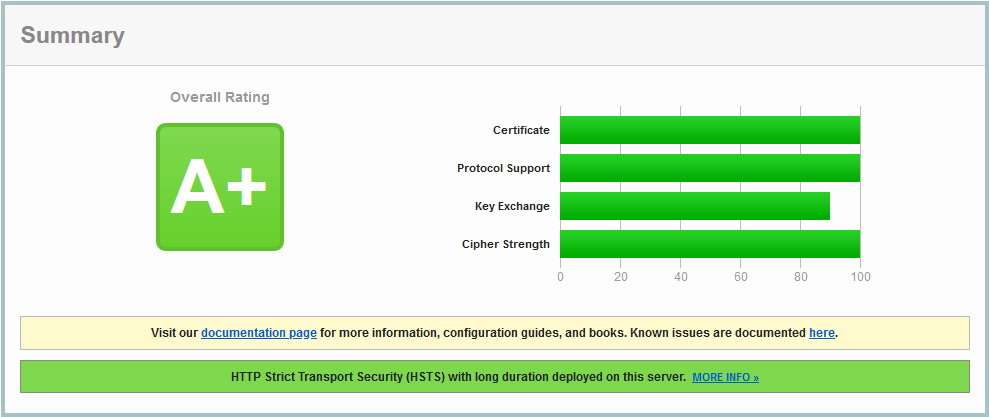
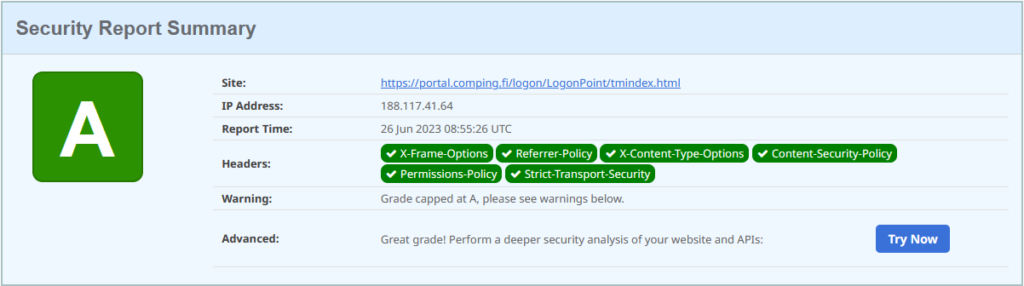
As these tools are available for the public, it’s clear that internet vandals are able to use them as well as other tools with which they’re able to scan a number of sites and recognize know exploits. Also; I’d say that if your security posture is handled it’s likely that the vandal will move to the next target.
Change management
Make sure your change processes are streamlined and you have the readiness to act quickly if your security is compromised. There are plenty of good examples of high graded vulnerabilities that are found from different vendors software at “difficult times” (holiday season) that need to be urgently patched or a configuration change needs to be applied to the environment asap to keep it running.
Why should I care?
Accountability – If you’re working in IT like me – it’s our responsibility to either fix or mitigate known vulnerabilities or if we’re not able to change things directly, we need to make sure that the decision makers are aware of these things. Eventually if something goes wrong, someone needs to prove they have done everything in their power to avoid problems from occurring.
Professional pride – Calling oneself a professional holds a certain value to it. In IT, making sure security is covered is a built-in part of the job.
Timeline – I think it goes without saying, preparing and preventing the issues in advance is way less expensive and less harmful for the business than fixing them after an attack has already happened.
What should I do?
Contact Comping!
Comping provides a service called Instrument for Access, which enables a managed and an easy way to get protected. The examples above merely scratch the surface of what we’re able to deliver for you.
Naturally we also provide consultancy services for our customers which might just be what you’re looking for!
You can also drop me an email (kari.ruissalo@comping.fi) if you have any questions or comments!

Check these articles
For the most part we rely on the vendors recommendations and stuff we have learned on the way. You may check some related articles from below:
NetScaler SSL / TLS Best Practices, https://community.netscaler.com/s/article/Networking-SSL-TLS-Best-Practices
Citrix TIPs: Scoring an A+ with HTTP headers and Citrix Gateway, https://www.citrix.com/blogs/2021/08/31/citrix-tips-scoring-an-a-with-http-headers-and-citrix-gateway/
Word of advice though; if you’re running any legacy endpoints or have some other variables in your environment that might get impacted by strenghtening your security posture, be careful.